The SSH (Secure Shell) network protocol is one of the most common tools for remote connection to a VPS/VDS virtual server. Despite all the advantages of this development, there are a number of difficulties in securing the SSH server.
A common mistake is to use SSH protocols without first configuring them. This usually results in the computer and connected server being hacked.
Any unauthorized user can without much effort disrupt the system operation (for example, using DDoS attacks), if connection via SSH is not secure.
Next, we are going to consider some reliable tips for securing SSH when using a Linux server. This will make working with VDS more efficient.
1. Creating SSH profiles

We recommend creating a special SSH profile if you are connecting to a Linux server which uses a Unix/Linux operating system. This will make the operating cycle performance much easier.
Programmed SSH configuration file will allow you to virtually connect to the device using only the profile name.
To connect from Linux to Linux
Creating an SSH profile requires the use of the ssh command as:
ssh [USERNAME]@[IP_ADDRESS] -p [PORT_NUMBER]
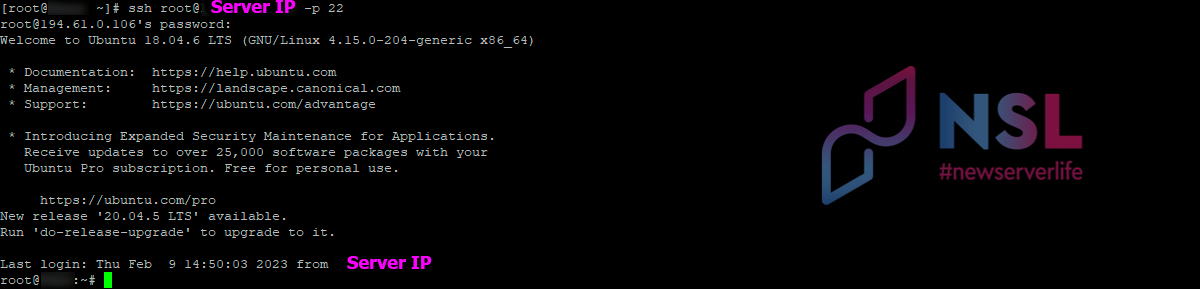
The exit command is used to disconnect from the server

SSH profiles are stored in the "~/.ssh/config" file.
Certain operating systems require you to create a "config" file manually using next command:
touch ~/.ssh/config
To connect to another server, you need to enter SSH profile data into the “~/.ssh/config” file. For example, the vi editor and the corresponding command will help you with this:
vi ~/.ssh/config
Configuration file should look like:
Host [PROFILE_NAME]
Hostname [IP_ADDRESS]
User [USERNAME]
Port [PORT_NUMBER]

Next command will allow you to access the VPS using just the profile name:
ssh [PROFILE_NAME]
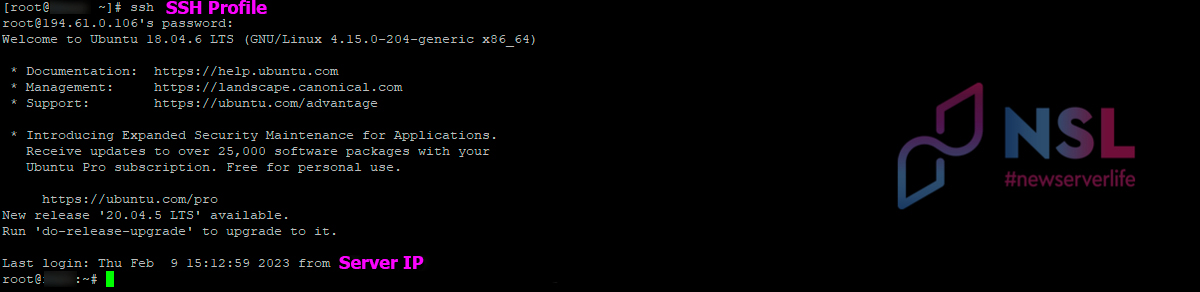
To connect from Windows to Linux
Creating such a profile in PuTTY is quite similar to creating it for Linux client.
Session data is entered when a remote SSH connection in PuTTY. They are saved in the main section Session → Saved Sessions under a separate name.
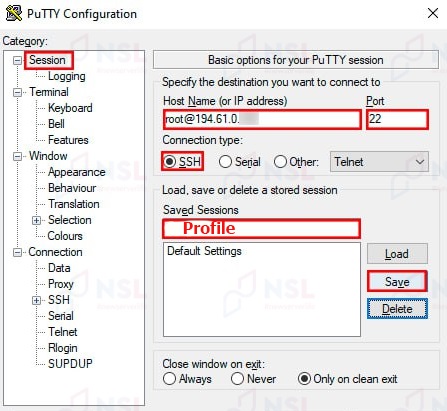
For easy and quick connection to a specific SSH server, you can use this saved profile. You just need to:
- open a saved session in the Saved Sessions section,
- enter the password in the opened terminal.

2. Connection without a password

You will have an opportunity not to enter a password each time you log in if a public/private key pair (SSH keys) has been created.
To connect from Linux to Linux
SSH connection by key is carried out according to several steps:
-
At first, you need to generate some SSH keys on the local machine (to set filename, location and passphrase).
ssh-keygen -t rsa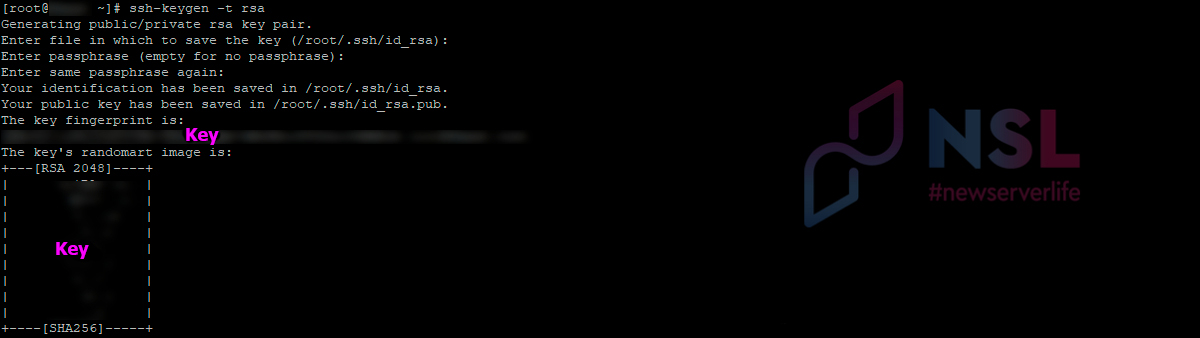
-
Next step is to copy generated key to remote server. You need to use the command:
ssh-copy-id [USERNAME]@[IP_ADDRESS] -p [PORTNUM]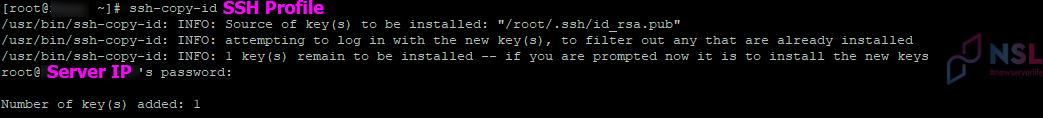
-
In the configuration file "~/.ssh/config" you need to add next lines:
Identitiesonly yes
Identityfile ~/.ssh/id_rsaThis is necessary so the connection could be carried out via an SSH profile without entering a password.
After completing all these steps, the system should be logged in without requiring a password.
To connect from Windows to Linux
Ready-made profiles (SSH keys) are used to quickly and easily connect via SSH without a password to the VPS.
3. Change the SSH port number
To hide the VPS from scanning you can change the port number (default port number 22). Any numbers from 1024 to 65 535 are available.
-
You can replace the SSH port number in "/etc/ssh/sshd_config".
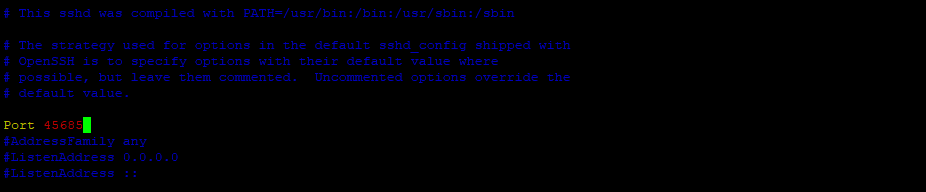
-
Then you need to restart sshd.service with the command:
sudo systemctl restart sshd
4. Blocking unused ports
To block unused ports in Linux you need to perform the following steps in the given order:
-
Open SSH port:
sudo ufw allow ssh -
Block port:
sudo ufw deny [UNUSED_PORT] -
Activate firewall:
sudo ufw enable -
Check firewall status:
sudo ufw enable
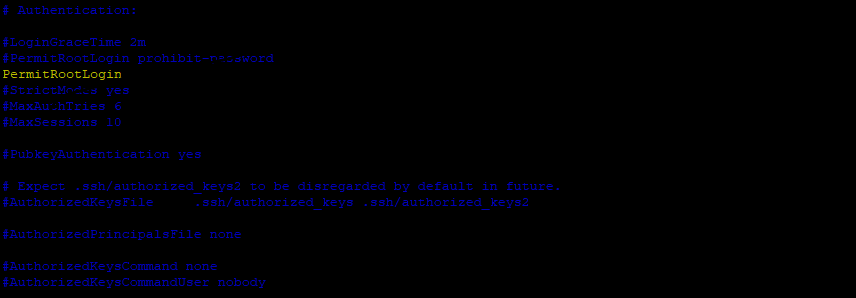
5. Block root access

To avoid unplanned changes on the server, it is recommended to block root access. This is an efficient method as access for new admin users is limited.
Root access lock requires performing next steps:
-
Add new admin user (just an example):
sudo useradd -m admin -
Create and set a new password for this user:
sudo passwd admin -
Add the user to a "sudo" list:
sudo usermod -a -G sudo admin -
The PermitRootLogin parameter must be set to "no", for access to be denied.
-
Next, you need to restart the sshd service using the command:
systemctl restart sshd
6. Blocking ping requests

The ping service performs several functions:
- Often used to check if a server is reachable at a specific IP address.
- Responds to ICMP packets requested from the client.
At the same time, this service can be used by robots to track the IP address of a specific server. This leads to a weakening of the protection of its privacy.

Algorithm of actions for deactivating ping (executed by a user with root access):
-
Open the configuration file "/etc/sysctl.conf":
vi /etc/sysctl.conf -
In the configuration file set the value:
net.ipv4.icmp_echo_ignore_all = 1 -
Apply ready changes with the command:
sysctl -p
Using the ping command, you can check that the server is not responding to ping requests anymore.
7. Disable X11/TCP port forwarding
This recommendation is useful, as hackers can use this weakness to connect to other network systems. You need to:
-
Open the domain configuration file and find next two lines:
AllowTcpForwarding yes
X11Forwarding yes -
Change these lines to:
AllowTcpForwarding no
X11Forwarding no -
Save and close this file.
8. Make a backup copy of the configuration file
Backing up the configuration file is a common practice to help in case of a mistake while editing the file.
To perform a backup, you need to use the command:
cp /etc/ssh/sshd_config ~/sshd_config_original
9. Performing commands via SSH
SSH allows users to add necessary commands at a moment of connection attempt. After executing the command, the connection is closed.
The basic syntax to help you understand how to execute a command over SSH is:
ssh [USERNAME]@[IP_ADDRESS] "command"
Examples:
-
Extract file from remote system with compression:
ssh [USERNAME]@[IP_ADDRESS] "tar -czf /projects" > ProjectBackup.tar.gz -
Check package installation status:
ssh [USERNAME]@[IP_ADDRESS] "rpm -qa | grep nano"
A pseudo-terminal with the -e command must be used when prompting for a password if you want to improve privileges on the server side of an SSH connection with sudo:
ssh -t [USERNAME]@[IP_ADDRESS] "sudo yum install nano"
10. SSH as a tunnel for other apps

SSH protocol performs several additional functions. One such feature is an encrypted and authenticated connection to remote devices for other applications.
If a graphical user interface (GUI) is required to complete a necessary task, you will need a VNC (Virtual Network Computing) – remote access system. For better privacy protection, you can tunnel the VNC connection over SSH.
For the "VNC over SSH" (HTTP-over-SSH) tunnel to work, you should forward ports using the following command:
ssh -L 5901:localhost:5901 -N -f user01 server01
Using the same method, you can set up an HTTP-over-SSH tunnel to a directory named "images". You need the command:
ssh -L 11000:localhost:80 -N -f -l [USERNAME]@[IP_ADDRESS]
Then launch a web browser and connect to http://localhost:11000/images.
11. Set connection timeout
To manage idle SSH connections in the configuration file, ClientAliveInterval directive is used.
The server directs a message to the user and waits for a response. ClientAliveInterval specifies the amount of time between these messages.
The connection is terminated at the moment when the ClientAliveCountMax directive determines the server's decision that the client is actually no more.
An example configuration that checks the performance every 60 seconds and does this three times:
ClientAliveInterval 60
ClientAliveCountMax 3
12. Limit the number of authorization attempts
Since there are an unlimited number of login attempts on a Linux server, hackers can use this to hack the system using a remote SSH connection.
However, there is a way to avoid this kind of situation. By specifying the number of password attempts allowed, you can set SSH connections to auto-terminate (after all allowed attempts are over).
To complete this task, you need to change the value of "MaxAuthTries" in the configuration file "sshd_config". For example, limit connection attempts to two:
MaxAuthTries 2
13. Limit SSH access to specific IP addresses
Restricting all SSH logins to specific IP addresses can be done using the following algorithm:
-
Open the "hosts.allow" file with the command:
sudo vi /etc/hosts.allow -
Next, you need to add a line that includes all IP addresses that are allowed to login via SSH:
sshd: 192.168.1.62, 192.168.1.11, 192.168.1.100 *(* just an example, you need to use your IP address).
- Save and close the file.
-
Open the "hosts.deny" file using the command:
sudo vi /etc/hosts.deny -
Add the following line below this file:
sshd: ALL - Save and close the file.
Conclusion
The implementation of the above methods to protect Linux servers anyway requires certain knowledge in the technical field.
It is also important to remember the need for comprehensive methods, since the use of a limited number of measures is unlikely to solve the problem of information security threats.
In certain cases, it is recommended to contact a specialist, since when working with a VPS, even a minor mistake can, in the worst case, lead to a complete loss of access to the server.
Specialists of our company are ready to help you purchase the server and select the necessary server configuration for any required task.