What is the OSI model
Today, the OSI seven-layer model is still a very popular basis that is used to build network interaction in all computer systems.
OSI (Open Systems Interconnection) is a specially developed model, the main function of which is to build a logical diagram of interaction between computer systems, which allows them to freely interact with other similar systems.
No less important functions of this model are the determination of the logic of network operation and efficient description of the computer packet transmission using protocols of various levels. In other words, the main purpose of the OSI model is to provide a visual explanation of how various elements and technologies interact to transmit data over a network.
History of creation

The idea of creating the OSI model arose after realizing the need for a reliable tool for visualizing the various components of a network system. Computer systems needed a universal way to interact with various companies and areas of activity (including business processes). As a result, the OSI model provided a reliable way to describe and analyze network structures.
Initially, 2 large projects were in the development process:
- International Telegraph and Telephone Consultative Committee (CCITT).
- International Organization for Standardization (IOS).
In 1983, all prepared documents were combined, and in 1984 ISO published them as a single framework. It was named OSI (Basic Reference Model for Open Systems Interconnection).
Thus, OSI Model has become a recognized international standard, which is not inferior in popularity to the most popular standard among network equipment manufacturers – TCP/IP model.
Differences between OSI and TCP/IP models
TCP/IP model was developed in the 1970s. Transmission Control Protocol (TCP) and Internet Protocol (IP) are the basis for the name of the TCP/IP model.
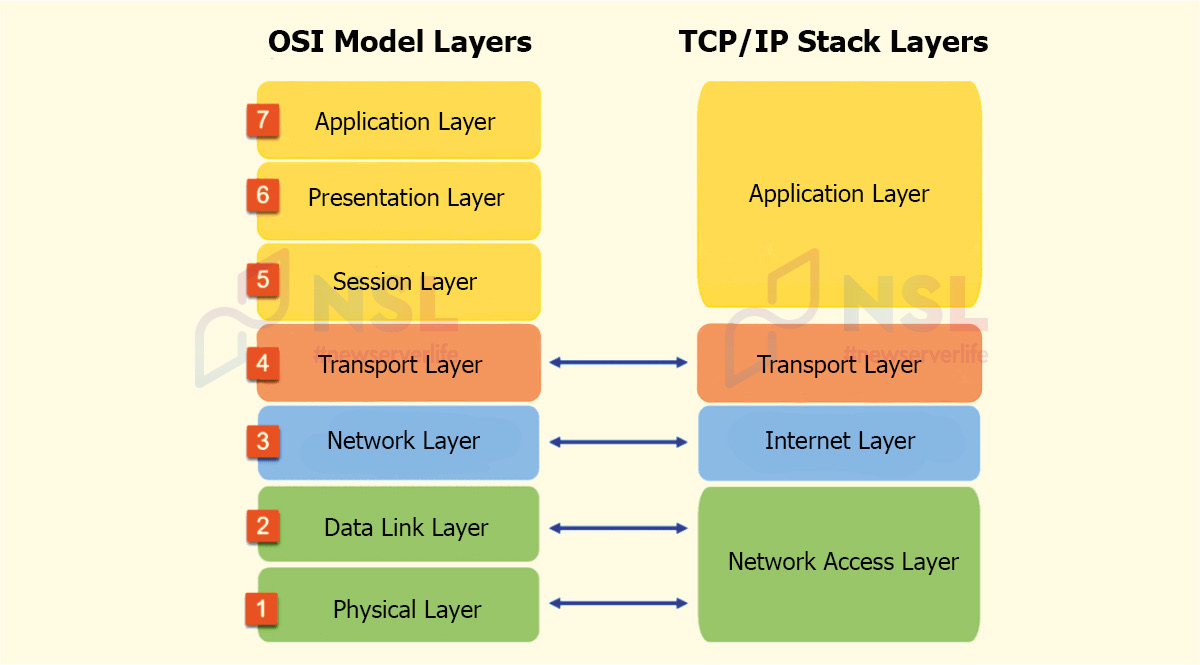
Let's consider the first difference – the number of levels.
- OSI has seven layers.
- TCP/IP combines OSI layers 1-2 into the network interface layer and OSI layers 5-7 into one application layer.
OSI is a more general model (describes network interaction in general).
TCP/IP model simulates the operation of communication protocols with maximum accuracy (it is an excellent option for public networks).
Next difference – work profile.
- TCP/IP is better for practical operations (all levels of this model can be used by appropriate applications.
- The OSI model allows applications to use only a few layers (layers 1-3 are required for data transfer).
OSI model operation
This process can be visually represented as follows:
There are two servers whose interaction requires data exchange. To do this, data blocks travel down the network layers and eventually reach the transmission line. This process must also be performed in reverse order (until it reaches the receiving app).
Next, we will consider several basic concepts that can be used to explain the data path:
- Service Data Units (SDU). They indicate the content of adjacent upper-layer PDUs, which is equivalent to the payload when transmitted to the lower network layer.
- Protocol Data Units (PDU). They are transmitted between equivalent network objects. They include protocol-specific and user data (+Protocol body / payload, + Protocol header, + Protocol trailer).
With each subsequent transition from some level N to any other level N-1, the level N PDU becomes a new N-1 SDU. This payload may be located in a level N-1 PDU including appropriate trailers and headers. Data travels up the chain at the opposite end. In the transition process they unfold at each necessary stage until they become just a payload. This payload can be used by an appropriate level N device.
OSI Model layers and their functions
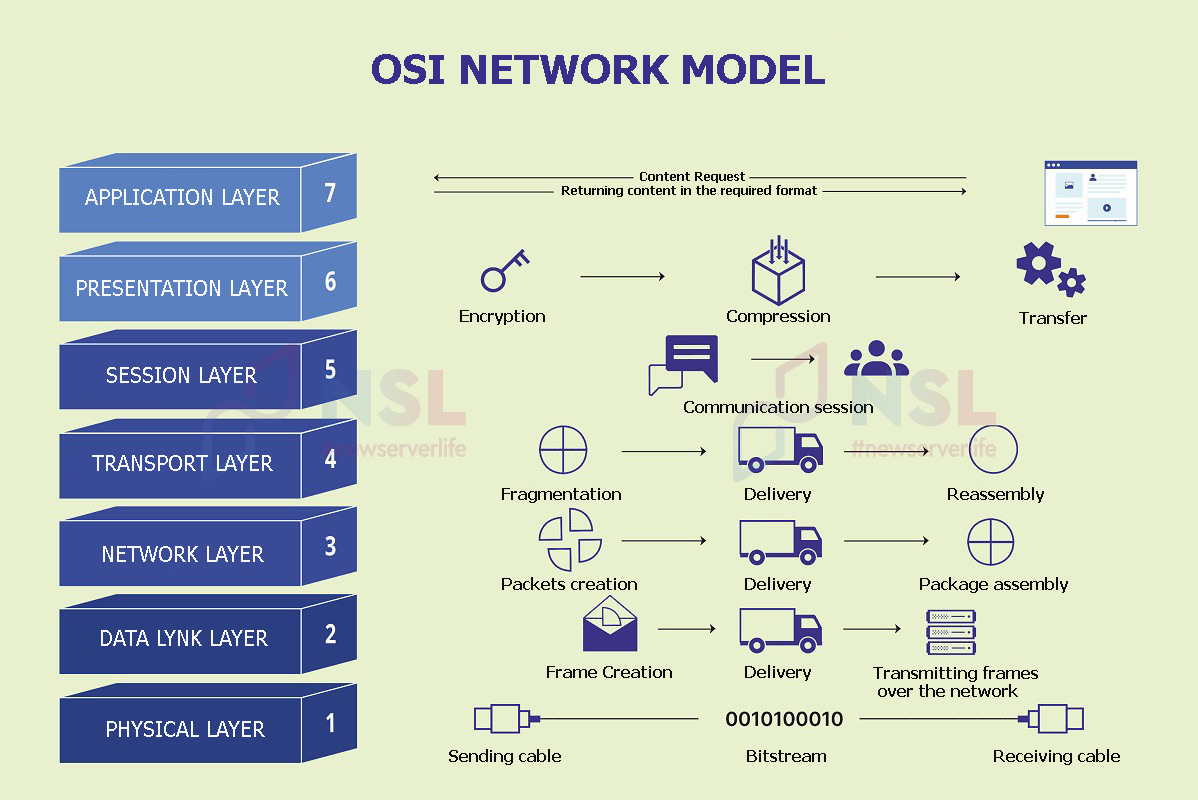
There are 7 separate layers of the OSI network model, which are united by a common protocol stack. General rules and guidelines are the basis of each level. They simplify the processes of creating and operating network technologies.
Each OSI model layer is essentially an associated critical data transfer process. Steps in such a path may include packet creation, flow control, encryption and presentation.
Layers in the OSI model describe the stages in which an idealized data packet passes through a communications system. More often, data is transferred from the L-7 OSI Application Layer down to the L-1 OSI Physical Layer. After that, they are transmitted in reverse order to the L-7 OSI layer. At the top level the data can be used by recipients.
L-7 OSI Application Layer

Data transfer format (PDU): message.
Purpose: to provide the user with access to network resources.
Basic protocols: Domain Name System (DNS), Hypertext Transfer Protocol (HTTP), Simple Mail Transfer Protocol (SMTP), Secure Shell (SSH), File Transfer Protocol (FTP), Simple Network Management Protocol (SNMP), Telnet.
This level is characterized by user interaction with data. L-7 makes it possible to receive data for use by software (or another option – preparing data before sending it through the chain of layers of the OSI model). The application layer of the OSI model includes software (it allows network applications to function).
Important L-7 OSI functions:
- Directory services.
- Working with protocols and data formatting tools.
- Post services.
- FTAM (File Transfer Access & Management) – access to file transfer and management.
- Network virtual terminal.
L-6 OSI Presentation Layer
Data transmission format (PDU): message.
Purpose: translation, encryption and compression of data.
Basic protocols: Transport Layer Security (TLS), MPEG Media Transport Protocol (MMTP), Multipurpose Internet Mail Extensions (MIME), Asymmetric Synchronous Channel Hopping (ASCH).
Raw data is located on the Presentation Layer. The main job of this layer is to process the data before it can be used by the OSI application layer. At this level, necessary data is encrypted and compressed (or vice versa, decrypted and unpacked). This process ensures secure data transfer. Transfer of large amounts of data at high speed is ensured by its compression.
Important L-6 OSI functions:
- Compression—reducing the number of bits transmitted over a network.
- Data conversion.
- Data encryption/decryption using a key value.
L-5 OSI Session Layer
Data transmission format (PDU): message.
Purpose: opening, managing and closing a session.
Device: network gateway.
Basic protocols: Session Announcement Protocol (SAP), Network Basic Input/Output System (NetBIOS).
The main purpose of L5 OSI is to define the rules for data transmission and authentication. The Session Layer also performs the function of establishing communication between devices. L5 OSI determines the accuracy of data transfer and the duration of sessions. It is also necessary to mention data checkpoints or data synchronization points. Checkpoints are used to divide data into smaller segments. Before closing the session, each segment is checked for correctness and reliability.
Important L-5 OSI functions:
- Data synchronization using checkpoints.
- Security (it is necessary to quickly end sessions and enable the authentication system).
- The most efficient data transfer with minimal use of resources.
- Dialogue controller (2 systems can communicate in half-duplex or full-duplex mode).
OSI Session Layer Tools:
Application toolkit can be applied by users. For example, let`s consider the FileZilla FTP application: it offers logs and debug menus, which helps resolve FTP connection problems at the session level.
L-4 OSI Transport Layer
Data transfer format (PDU): fragment.
Purpose: Transfer data from a process on the source computer to a process on the target computer.
Device: network firewall.
Basic protocols: User Datagram Protocol (UDP), Transmission Control Protocol (TCP).
L-4 OSI is responsible for setting up direct communication between connected devices. Its main task is to ensure continuous data transfer (they must be sent and received in the same form).
Special tools used at this layer determine the correct data transfer rate (taking into account the connection speed of the devices used, data transfer speed may vary). The OSI transport layer controls the flow of data in end-to-end communications.
Important L-4 OSI functions:
- Error control by evaluating data packets at the receiving device. L-4 OSI service providers may request retransmission if the data did not arrive in the correct form.
- Segmentation and reassembly. The received message from a higher level is divided into smaller blocks (each of these blocks has a header associated with it). At the final destination, all fragments are reassembled into a message.
- Service Point Addressing. The L4 OSI header has an address type called service point address or port address (ensures that the message is sent to the correct process).
OSI Transport Layer Tools:
For Linux, separate solutions are used for certain protocols, since no special tools have been developed. For TCP there is a utility tcptrack, which performs the function of displaying lists of current sessions. tcptrack can be installed using the apt command:
sudo apt install tcptrack
To make active interface connections available, you must use the -i option and the interface name:
sudo tcptrack -i eth0
Monitoring of outgoing and incoming packets on a specific interface is available thanks to the tcpdump packet analyzer. The eth0 interface is used by default. The -i attribute displays the listening interface:
sudo tcpdump
L-3 OSI Network Layer
Data transmission format (PDU): packet.
Purpose: data transfer from one host to another on different networks.
Device: router.
Basic protocols: Internet Group Management Protocol (IGMP), Internet Protocol (IP), Internet Control Message Protocol (ICMP), Multiprotocol Label Switching (MPLS), Border Gateway Protocol (BGP), Open Shortest Path First (OSPF).
The main task of L-3 OSI is to create and support the stability of network connections. The OSI Network Layer performs the function of transferring data between connected devices. The data is divided into packets ready for transmission over the network. The original data is restored by combining packets at the receiving end of the transmission
Important L-3 OSI Functions:
Logical addressing – placing the sender and recipient IP addresses in the header helps define the addressing scheme for each unique device on the network.
Routing – hardware and software determine the optimal path for transmitting data between various networks.
OSI Network Layer Tools:
For any problems at network level, the ip command is useful. The ip addr show command shows the IP address associated with each interface:
ip addr show
To view the contents of the system routing table the following command can be used:
ip route show
ping and traceroute commands help you track the path along which a packet is sent to its destination. They can be used with the IP address or router name:
ping wikipedia.org
L-2 OSI Link Layer
Data transmission format (PDU): frame.
Purpose: organize bits into frames to enable local data transfer.
Device: network bridge (switch).
Basic protocols: Asynchronous Transfer Mode (ATM), Rapid Assessment of Physical Activity (RAPA), Frame Relay (FR), Point-to-Point Protocol (PPP), fiber optic cable.
The L-2 OSI layer is closely related to the Network layer. However, it is most often referred to as communication between locally connected devices.
At this level, after receiving, all data is divided into frames. These frames interact with two sublayers of the L-2 OSI layer:
- Media Access Control (MAC) – connects appropriate local devices and controls the flow rate on the network.
- Logical Link Control (LLC) – establishes the logical basis for local data transfer.
Important L-2 OSI Functions:
- Access control (determining control priority between used devices).
- Framing (transmission of the desired set of data is possible by attaching specific combinations of bits to the beginning and end of the frame).
- Data rate control (competent distribution of information flows).
- Physical addressing (adding the MAC address of the sender and/or recipient to the headers of created frames).
- Error control mechanism (transmission of data containing any errors will be repeated).
OSI Link Layer Tools:
To display information about network interfaces on the server, you will need the next command:
ip link show
The nast packet utility can be used to analyze local network traffic. This utility can be installed using the apt command:
sudo apt install nast
Next step – you should run the command with superuser rights and specify the interface to listen to using the -i parameter:
sudo nast -i eth0
The configuration and capabilities of each network interface can be viewed using the following command:
ip netconf
L-1 OSI Physical Layer
Data transmission format (PDU): bit.
Purpose: providing electrical and mechanical resources for transmitting bits in networks.
Devices: modem, RF links, cables, hub, repeater, voltage regulators and routing devices.
Basic protocols: Integrated Services Digital Network (ISDN), Recommended Standard 232 (RS232/EIA232), 100BaseTX.
The L-1 OSI layer includes all physical infrastructure and necessary equipment used to transmit data. The digital bit stream that is converted to L2 OSI is formed from 1s and 0s at the physical layer. Before transmission, the form of this bit stream is confirmed between the two devices. This makes it possible to reconstruct the data at the receiving end.
The most common errors and network problems occur at the physical OSI layer, but they can be eliminated quite simply.
Important L-1 OSI Functions:
- Selecting a data transfer mode (simplex, half duplex and full duplex modes are included).
- Synchronization of sender and receiver bits.
- Determination of the physical topologies of network devices.
- Data transfer rate control.
OSI Physical Layer Tools:
There are no practical ways to debug problems at this level. Eliminating existing problems usually requires a series of trial and errors in the process of replacing physical ports, connectors and cables.
Cross-level functions
Cross-layer functions are different layers combined in the OSI hierarchy. These functions include the most important services for certain parts of the data transfer process. Some of these services include:
- Common security architecture recommended by ITU x.800 standard.
- Protocols for converting IP addresses to MAC addresses (they operate at the network and data link layers).
- Security management tools for configuring and controlling the process of data exchange between network devices.
- Domain Name System (DNS) lookup services.
- Multi-protocol label switching (MPLS) for transferring data frames between networks.
Cross-layer functions monitor and regulate traffic, ensuring secure and reliable data transmission. Cross-layer functions operate at different network layers and resolve problems as they arise. Thus, cross-layer services are the basis of network security planning.
The process of transferring data across the layers of the OSI model
L-7 OSI. At the Application Layer, the web browser client interacts with the application protocol. The user's request takes the form of an HTTP or HTTPS message. The DNS protocol applies to resolving a domain name to an IP address.
L-6 OSI. When using HTTPS, the Presentation Layer encrypts the outgoing request with the help of TLS socket. The data may also be encoded or translated into another character set.
L-5 OSI. At the Session Layer, a session is defined for sending and receiving HTTP/HTTPS messages. Because web browsing requires reliable data transmission, the L-5 OSI layer most often opens a TCP session. Some streaming applications may also choose a UDP session for use.
L-4 OSI. The Transport Layer TCP protocol initiates a connection with the target server. During a session, packets are transmitted in their original order, as well as being sent and received. UDP sends all packets without a direct connection and without waiting for confirmation. In some cases, data packets may be segmented into smaller parts. Further, all outgoing packets are sent to the Network layer.
L-3 OSI. Routing protocols select the output interface to use based on the destination address. The data, including address information, is encapsulated in an IP packet, which is then forwarded to the Link Layer.
L-2 OSI. The link layer converts IP packets into frames (this may lead to their fragmentation). Frames are created based on the data link protocol, which is used.
L-1 OSI. At the physical layer, frames are converted into a stream of bits and transmitted to the media.
OSI model and DDoS protection
The OSI Network model is the primary method for countering serious cyberattacks such as DDoS. Each OSI layer is distinguished by certain types of DDoS attacks and methods for eliminating them:
L-7 OSI. Common types of DDoS: "slow session" attacks, hacking the BGP protocol, HTTP(S) GET/POST flood. Protection methods: monitoring applications and tracking zero-day attacks and cyber attacks at this OSI layer.
L-6 OSI. Common types of DDoS: sending false or incorrect SSL requests. Protection methods: cleaning, filtering, and routing SSL traffic.
L-5 OSI. Common types of DDoS: attacks through vulnerabilities in network protocols for terminal interfaces. Protection methods: regularly updating software versions, restricting access to network equipment.
L-4 OSI. Common types of DDoS: SMURF attacks, SYN flood (TCP/SYN), UDP flood. Protection methods: filtering and limiting the number of connections from certain sources.
L-3 OSI. Common types of DDoS: SMURF attacks, POD (ping of death), ICMP flood (ping flood). Protection methods: using heuristic algorithms, false traffic is filtered and redirected.
L-2 OSI. Common types of DDoS: manipulation of data in the SRC/MAC and DST/MAC fields leads to disruption of the standard network data flow between devices. Protection methods: applying modern managed switches.
L-1 OSI. Common types of DDoS: any damage to the equipment or disruption of its performance. Protection methods: using the system for restricting and controlling access to equipment.
OSI Model Advantages
Cybersecurity. The OSI system makes it possible to identify security weaknesses. Information security specialists classify risks in accordance with OSI levels, which allows them to select suitable data protection tools after determining data location in the network hierarchy.
Troubleshooting. The OSI hierarchy makes it possible to detect network defects at an early stage. This model can be used by professionals to detect application problems, network-wide problems, or physical hardware failures. OSI offers a reliable way to divide problems into manageable parts.
Software development. The OSI model plays an important role in the planning and coding stages. Applications operating at different levels can be simulated by specialists. The layer model defines an algorithm for interaction of the application with other network components and tools from different vendors.
Marketing. By providing detailed product feature descriptions, marketers can accurately explain to customers where their products fit in the OSI hierarchy. Buyers can figure out how these products will fit into the network architecture.
OSI Model Disadvantages
- There is a bit of chaos due to the fact that certain functions span different OSI layers.
- Presence of redundant elements in the 7-level model is also a minus.
- Statements by many experts that the OSI system is outdated. It is believed that today the division of network structures into seven different levels is not effective anymore. The Internet is less compliant with the OSI model, which is why it never became the main industry standard among network equipment manufacturers.
Conclusion
Although OSI is a convenient learning model, it is rather abstract in nature. The OSI model protocols are most often used in conjunction with the TCP/IP stack.
However, a large number of popular network tools still map to different OSI layers, making the OSI model an essential part of many network techniques. Moreover, the conceptual principles of this model can be the basis for creating cybersecurity systems and protection against distributed network attacks.
Let's not forget that OSI became a successful result of an attempt to standardize a network language. This gave experts a common language to discuss IT network architecture. This hierarchy also made it easier to compare hardware profiles, protocols, applications, etc.
Thus, the OSI model is still relevant in many areas of activity and is used all over the world.
Specialists of our company are ready to help you purchase the server and select the necessary server configuration for any required task.

























































